Conditional Remix & Share Permitted
CC BY-NC-SA
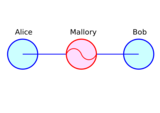
This is an unplugged version of how a man in the middle attack can happen and how data can be altered using rope, binder clips, envelopes and index cards.
- Subject:
- Computer Science
- Cybersecurity
- Networking and the Internet
- Material Type:
- Activity/Lab
- Homework/Assignment
- Author:
- Ronald Sparks
- Date Added:
- 05/24/2022