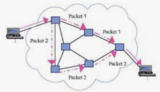
This activity will help students understand how computer packets of information travel through a network.
- Subject:
- Networking and the Internet
- Material Type:
- Activity/Lab
- Author:
- Kimberly Emory
- Date Added:
- 05/20/2022

This activity will help students understand how computer packets of information travel through a network.

This Google Slides contains a Packet Switching Activity. Students will model how data trassmission across the Internet uses packet switching.

Reporting the Weather: Students using the power of our local network weather station to forecast, record, and share weather data.

In this first part of a three part series, students will explore the ideas around Brute Force algorithm/programs to further understand the importance of password development, use, safety, and safekeeping while completing several unplugged activities over the course of three class periods (approximately 30-45 minutes each). These activites can be completed seperately with a few adjustments as well. Part 1 introduces Brute Force using a playing cards demonstration to sort as desired. Part 2 introduces Decrease (or Divide) and Conquer to sort Quadrilaterals from Non-Quadrilateral shapes. Part 3 uses the methods of both Brute Force and Divide and Conquer algorithms to decrypt (unscramble) passwords using commonly recognizable number patterns and words (completed on paper, or unplugged). These activitess are intended for upper middle school students, but could also be adjusted for lower level highschool or simplified/adjusted for other ages as well with the editable copies provided.
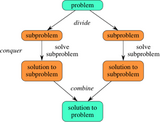
In this second part of a three part series, students will explore the ideas around Decrease, or Divide, and Conquer algorithm/programs to further understand the importance of password development, use, safety, and safekeeping by completing several unplugged activities over the course of three class periods (approximately 30-45 minutes each). These activites can be completed seperately (stand-alone) with a few adjustments as well. Part 1 introduces Brute Force using a playing cards demonstration to sort as desired. Part 2 introduces Decrease (or Divide) and Conquer to sort Quadrilaterals from Non-Quadrilateral shapes. Part 3 uses the methods of both Brute Force and Divide and Conquer algorithms to decrypt (unscramble) passwords using commonly recognizable number patterns and words (completed on paper, or unplugged). These activitess are intended for upper middle school students, but could also be adjusted for lower level highschool or simplified/adjusted for other ages as well with the editable copies provided.

In this final part of a three part series, students will practice Brute Force and Decrease (or Divide) and Conquer methods to try to crack a password puzzle to further understand the importance of password development, use, safety, and safekeeping by completing several unplugged sorting activities over the course of three class periods (approximately 30-45 minutes each). These activites can be completed seperately with a few minor adjustments as well. Part 1 introduces Brute Force using a playing cards demonstration to sort as desired. Part 2 introduces Decrease (or Divide) and Conquer to sort Quadrilaterals from Non-Quadrilateral shapes. Part 3 uses the methods of both Brute Force and Divide and Conquer algorithms to decrypt (unscramble) passwords using commonly recognizable number patterns and words (completed on paper, or unplugged). These activitess are intended for upper middle school students, but could also be adjusted for lower level highschool or simplified/adjusted for other ages as well with the editable copies provided.

This lesson gives students a very basic introduction to the data transmission concept of packets and how data is broken down, transmitted across a network, and then re-assembled into a final product.

Create different quadrilaterals using the geoboard and use these shapes to show how information can be transmitted in different ways via a network.

This is a game on Quizalize.com based on the Computer Science standard 6.13 on data types and transmission speeds. The students will click the link to take them to the game. The questions can be read aloud to the students.
Play a technology enhanced version of the classic telephone game. Use a discussion board to post the the message, then compare it to the original.

Networking and the Internet4.18 The student will identify and explain different ways information can be transmitted using computing devices via a network (e.g., email, images, and videos).This informational sheet includes examples of communication that can be transmitted across networks and gives students an opportunity for small group discussion.Please download the PDF

Have you ever wondered how we keep our Chesapeake Bay watershed clean? Come view this 360-degree video on the Chesapeake Bay program completing a clean up, and then explain why you believe that helping their program and networking their program will help keep the watershed clean in the future!

In this activity, students will interview a peer via video conferencing. Students will watch a brief Brainpop video on how to conduct an interview, review interview etiquette, and answer a questionnaire to better prepare themselves for the interview process.
Three days are recommended for the entire process. Day 1: Set up for the interview, Day 2: Group 1 interviews, Day 3: Group 2 interviews.
The class will be split into groups (Interviewer and Interviewee) or you can ask another class to participate with you - video "pen pals". The two groups will switch and play the reverse rolls.

In this activity/ lesson students will conduct research about a given or chosen profession, interview a professional in the field via video conferencing, and write a short article, essay, journal entry, or blog about their experience and the information they gathered.

Networking and the Internet2.15 The students will discuss with partners and as a class how information can be communicated electronically (e.g., email, social media, video conferencing, blogging).This sheet contains definitions and examples on how email addresses are formatted and used.

Learn about wildlife research conducted at the Wildlife Center of Virginia. Rehabilitators and veterinarians treat tens of thousands of wild animals each year and are often the first to notice trends that contribute valuable insights to overall wildlife health. During the past 37 years, Center veterinarians have led a variety of research studies on wildlife health, using data from the patients admitted to the hospital. Join the Center staff and other wildlife professionals to learn about the critical role wildlife rehabilitators and veterinarians play in caring for wildlife population health.
This is a writing prompt choice board intended to be used in a writing center or station. In my classroom we typically use one choice board per week. Students choose up to 4 items to complete for the week. I do 4 items to give students time to finish incomplete work on Fridays, to work on final drafts, to edit a selected item, or to share their writing with peers. You can make the rules for your classroom to best suit your teaching style and your student's needs.
The choice board includes 8 prompts and one Student Choice square based on Networking and the Internet standards for first grade.
Please feel free to make a copy of the choice board and edit it to meet your specifications.