
Compare and contrast the properties of quadrilaterals - Mathematics Instructional Plan
- Subject:
- Mathematics
- Material Type:
- Lesson Plan
- Provider:
- VDOE
- Author:
- VDOE
- Date Added:
- 10/07/2024

Compare and contrast the properties of quadrilaterals - Mathematics Instructional Plan

Compare and Contrast Quadrilaterals Formative Assessment - Just in Time Quick Check, Teacher Notes, and Supporting Resources

Deepen understanding of quadrilaterals - Rich Mathematical Task Template and Student Version

Determine Unknown Side Lengths or Angle Measures of Quadrilaterals Formative Assessment - Just in Time Quick Check, Teacher Notes, and Supporting Resources

Determine unknown side lengths or angle measures of quadrilaterals - Mathematics Instructional Plan
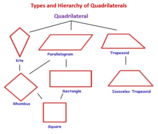
The students will visualize how the properties of Quadrilaterals can help them determine the exact shape of the figure. The students will create a model of the properties and compare them to the results the students have from data they have found

Students will find helpful resources for learning and practicing math skills and processes in this eMediaVA collection.

This collection has resources organized by grade level teachers can use to teach math.
Using the Virginia Museum of Fine Arts website, students explore the sculptural work of 20th Century Conceptual artist Sol LeWitt to expand their understanding of geometric concepts, creatively play with mathematical ideas, and be inspired to make art of their own.
The website page provides a scaffolded approach to exploring Sol LeWitt's sculpture titled "1, 2, 3, 4, 5, 6." culminating in a challenge for students to build a 3-D Tinkercad model of a geometry concept of their own choosing.
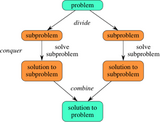
In this second part of a three part series, students will explore the ideas around Decrease, or Divide, and Conquer algorithm/programs to further understand the importance of password development, use, safety, and safekeeping by completing several unplugged activities over the course of three class periods (approximately 30-45 minutes each). These activites can be completed seperately (stand-alone) with a few adjustments as well. Part 1 introduces Brute Force using a playing cards demonstration to sort as desired. Part 2 introduces Decrease (or Divide) and Conquer to sort Quadrilaterals from Non-Quadrilateral shapes. Part 3 uses the methods of both Brute Force and Divide and Conquer algorithms to decrypt (unscramble) passwords using commonly recognizable number patterns and words (completed on paper, or unplugged). These activitess are intended for upper middle school students, but could also be adjusted for lower level highschool or simplified/adjusted for other ages as well with the editable copies provided.