
Students will use dominoes to represent how data can be manipulated on a computing device.
- Subject:
- Computer Science
- Data and Analysis
- Material Type:
- Activity/Lab
- Author:
- Robert Underwood
- Date Added:
- 04/08/2022

Students will use dominoes to represent how data can be manipulated on a computing device.

Students will play an interactive game while learning how to be internet smart. Students will learn the fundamentals of digital literacy: sharing, kindness, security, determining what's real and what's fake, and reporting. This game comes with a full curriculum guide: https://storage.googleapis.com/gweb-interland.appspot.com/en-us/hub/pdfs/Google_BeInternetAwesome_DigitalCitizenshipSafety_2019Curriculum.pdf
This is an Internet Safety Quiz built as a Google Form.
This is a lesson presented by Common Sense Education.
The lesson takes 35 minutes or there is an option for a "quick lesson" that takes 15 minutes.
In order to access the lesson, you will need to sign-up for FREE access. I used my google account to login - SIMPLE.
MATERIALS:
- All digital materials are included.
The slides mentioned below use google slides. All slides are in one presentation and can be downloaded or copied (copyright information is listed on the website).
TEACHER WILL NEED:
- Tape or long piece of string
- Green, yellow, and red pieces of construction paper
Learning Objectives:
Understand that being safe online is similar to staying safe in real life.
Learn to identify websites and apps that are "just right" and "not right" for them.
Know how to get help from an adult if they are unsure about a website.
Brief Overview:
The lesson plan covers 4 steps that can be broken up into smaller segments or done all together.
1. Explore - Go! Caution! Stop! (15 minutes) > this section includes teacher dialogue and premade slides to introduce how to choose a "just right" website
2. Read - Internet Traffic Light (5 minutes) > This is a poem to help students remember how to choose a "just right" website. The slide is premade for display and teacher directions are included.
""Internet Traffic Light" by Wren Brennan
We go online to find new things to do and see.
The internet traffic light shows where we need to be.
Green means GO! [hold up a green paper] to sites we trust.
Yellow means SLOW! [hold up a yellow paper] Being safe is a must.
Red means STOP. [hold up a red paper] Ask if it's OK.
Trust your gut to go the right way."
3. Play - Traffic Light Game (10 minutes) > Game instructions are included along with the slides to display.
4. Reflect - Pause and Think Moment (5 minutes) > Gives students a moment to draw a picture and write about what they would do if they accidentally went to a "not right" website. You can either discuss this as a whole group, make it a writing center for another day, or share thoughts with a partner.
Overall, this is a great lesson to help introduce cybersecurity and internet safety for early elementary students. It is beneficial that all materials, teacher script, and explanations are included.

Students will explore and understand the differences between local and worldwide networks, while integrating fraction concepts.
In this 30 to 45 minute lesson, students use Code.org's Artist Lab or Artist Lab (Pre Reader) to develop an understanding of Loops and practice their use in Computer programming.

Developed by the Science Museum of Western Virginia, this educator outline was written for an in-museum program that addresses computational thinking. Teachers and students in grades 3-4 will expand knowledge of computer science algorithms and programming content while working through the activities "Flossbot" and "Edison Bot Activity".
*Edison bots are used for the second activity.
Key concepts include:
computer science
coding
programming
binary
computer
robot
loop
bug/ debug

As technology becomes ever integrated into our food system and everyday life, our food industry and supply become ever more vulnerable to attack. Cyber attacks continue to threaten large and small companies, government agencies, individuals, and food and agriculture. This module, ‘Securing the Food Industry,’ aims to introduce the idea of cyberbiosecurity through a lecture format along with three case studies allowing students to interact and think through the concepts and materials. This module was built for implementation into college level courses with connection or interest in the food industry, food science, and agriculture as well as and technology courses focused on real world applications.
The lecture starts by introducing the amount of technology in food science and the food industry then transitions into concerns about security. After discussing multiple subtypes of security already integrated into the food industry, cyberbiosecurity is introduced. The term and definition are discussed before the categories of cyber attacks are introduced. The lecture relates these ideas back to the food industry before sharing a few real-life examples of detrimental cyber-attacks. The lecture concludes are explain the impact a cyber attack can cause, who is responsible for preventing and recovering from these attacks, as well as suggested practices to reduce vulnerabilities. Three theoretical but realistic case studies with discussion questions follow the lecture. These studies were written to act as small group discussion starters but could be used for whole class discussion, individual writing assignments, or other applications.
A list of additional resources can be found with the course material. This list provides a small sampling of additional documents which discuss cyberbiosecurity. The resources listed at the end of the lecture are not included in the additional resources document but also provide helpful information in the exploration and understanding of cyberbiosecurity. Food science resources are also included in this document to provide additional background around the food industry portion of this course material.
Securing the Food Industry is an open educational resource (OER). Instructors reviewing, adopting, or adapting the module should indicate their interest at https://forms.gle/orFRGhYs8owBP7gD6.

In this lesson, students engage in a historical jigsaw activity focused on westward expansion. The lesson ends with a coding project where students create “postcards” by coding with Twine, expressing the perspectives of different groups experiencing the effects of westward expansion.--

Students will use words and coding to work from a starting point to place colored squares on a grid and end at a location.
This lesson plan is a bacic introduction into what technology is and isn't , Cyber Security for the elementary student and an introduction into Digital Citzenship.
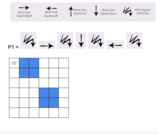
During this lesson, your students will be introduced to some foundational computer science concepts of sequence, pattern recognition, loops and procedures. Unplugged activities are a way to reinforce CS concepts that are introduced in coding apps and puzzle games like LightBot, Code.org, Kodable, etc.
This lesson is part of the Virginia K-12 Computer Science Pipeline which is partly funded through a GO Virginia grant in partnership with Chesapeake Public Schools, Loudoun County Public Schools, and the Loudoun Education Foundation. During this lesson, students will create a simulation of Earth's Enegy Budget using Scratch.

This is a slideshow showing second graders how to model their own water cycle. 2.12 The student will create a model of a physical object or process in order to show relationships with or without a computing device (e.g., water cycle, butterfly life cycle, seasonal weather patterns).Models are used to represent a system (or parts of a system) under study, to aid in the development of questions and explanations, to generate data that can be used to make predictions, and to communicate ideas to others
This lesson is part of the Virginia K-12 Computer Science Pipeline which is partly funded through a GO Virginia grant in partnership with Chesapeake Public Schools, Loudoun County Public Schools, and the Loudoun Education Foundation. In this lesson, students will create examples of gravitational potential and kinetic energy transformations using Scratch.
This lesson is part of the Virginia K-12 Computer Science Pipeline which is partly funded through a GO Virginia grant in partnership with Chesapeake Public Schools, Loudoun County Public Schools, and the Loudoun Education Foundation. In this lesson, students will create isotherms and isobars on weather maps.
This link will take you to a lesson on CSUnplugged.org. The lesson deals with the concept of network sorting.

The students will work with a partner or small group to design a program to move a “student” through a classroom with obstacles. Their job is to find the most efficient sequence of actions for them to get to the cafeteria from the classroom. The student will be a paper avatar. The classroom will be a 8 by 8 grid with pictures of obstacles the student must move through to get to different destinations. The students will try to move through with the least number of steps. As an extension, they can rename a loop of multiple steps, and it will become one step.
Jennifer Daniel of Washington County has created a Wakelet with lots of tutorials on using Schoology. Great for beginners, since it is new in their division this year.
Jennifer Daniel of Washington County gathered together some supporting resources for teachers using Google Classroom as their main classroom!