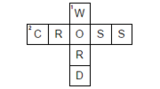
This is a crossword puzzle designed on Flippity.net that has the essential vocabulary from the Computer Science SOL 3.17 in Networking and the Internet.
- Subject:
- Computer Science
- Material Type:
- Activity/Lab
- Author:
- Dana Smith
- Date Added:
- 12/21/2021

This is a crossword puzzle designed on Flippity.net that has the essential vocabulary from the Computer Science SOL 3.17 in Networking and the Internet.
This activity, created on Quizalize, is from the essential knowledge and vocabulary from the Computer Science SOL 5.7, from the strand Computing Systems.

This is a matching game that utilizes the vocabulary from the Computer Science SOLs 7.8 and 7.9 from the Data and Analysis strand.
This game created on Gamilab is from CS SOL 8.9 and is titled, “Public and Private Information.”
It is a bike race game where students must correctly answer questions to advance regarding online information from the Computer Science SOL 8.9 from the strand of Impacts of Computing. To start, press the up arrow a couple of times. Please enter code G8471Tto play if you have any problems with the link.

These Pocket Guides are a quick summary of each of the 6 computer science strands for grades K-8. The pocket guides explain what the strand is about and how it increases in complexity from Kindergarten to 8th grade.

One of the fundamental computer science concepts is that everything we do on a computer is really just turning binary digits on and off. Even though this sounds simple, it can be a concept that is hard to wrap one's head around. This activity brings the binary concept to reality through the creation of binary bracelets or bookmarks.

With advances in AI, it is more important than ever that we consider how humans and computers will interact. How do you want the robots of the future to behave towards you and others? For this activity, students will make a “robot zine” where they will sketch an original robot design, identify how their robot will sense the world around it and write a code of conduct to describe how their robot will interact with humans.

Every day our privacy is at risk with data being collected about us as we share and live more of our lives online. For this activity, you will explore how you do and do not protect your privacy online and then create a security avatar to help you battle for your privacy.

This unplugged lesson will allow students to encrypt and decrypt message using the Caesar Cipher letter shift method of encryption. Cover the process of how this method works by doing an example and explaining the process of shifting the plaintext by the letter shift value to create the encrypted cipher text.

This lesson is designed to teach students basic encryption using the Caesar cipher method. This is a simple letter shift cipher that takes a plaintext message and encrypts it into cipher text by shifting each letter of the message by a value between 1 and 25 (1 less than the total number of letters in the English alphabet). This technique was used by Julius Caesar to encrypt messages by shifting each letter of the message by 3 letters. The message would be decrypted by taking each letter and shifting back 3 letters to reveal the plaintext message.
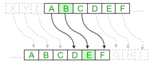
This lesson plan can be used for teaching and reinforcing the idea of encryption for middle school students.

The students will consider what it would be like to have someone use a favorite possession without their approval. The students will then learn what personal information is and why they should keep it private. At the end of the lesson, the students will determine what information is safe to share with others and what is not safe to share.

Introduce cause/effect and input/output to students, then complete a related scavenger hunt.

Students will understand digital citizenship and the role they play as digital citizens.

Students will apply their knowledge of the causes of the American Revolution to create an interactive story via Twine. The interactive story will be based on the pre-revolutionary war period from the point of view of a loyalist or a patriot. As a warm-up students will look at an optical illusion picture and as a class discuss point of view and perspective. Students will work in heterogeneous pairs/groups to research, outline, and create a pre-revolutionary story about a patriot or loyalist.

Students will examine the history and culture of the Choctaw Native Americans, as well as the story of the Code Talkers in WW1, in order to memorialize one of the Choctaw Code Talkers.

This presentation focuses on the hows and whys of using Choice Board and Hyperdocs. It is about 54 minutes long and the accompanying slide deck is included.

Create an American Revolution adventure story with your class! Students will be able to step back into time and think of the various perspectives of the American Revolution by creating scenarios the different characters might have gone through.

A common component most computing devices include is a keyboard (either physical or screen-based) for inputting information. A common computing device is a Chromebook which is similar to a laptop.Students will use a crayon to answer the questions for each Chromebook keyboard on the handout by coloring in the correct keys they would press on an actual Chromebook.

Students will be competing to win a “grant.” Students will be creating a Canva presentation about what battle of the Civil War was the most important. Students should include important dates, people, and details about the specific battle. The students will use a planning paper prior to starting their presentation to create a step-by-step plan for their presentation. Their presentation should give clear information (dates, people, and details) about why the battle site they chose is the most important battle of the Civil War. Students will share the load in their project and split tasks among group members. Each group will be assessed with a rubric.