
Explore the four main phases of the problem-solving process. Analyze a problem and use the steps in the problem-solving process to solve a problem.
- Subject:
- Computer Science
- Material Type:
- Activity/Lab
- Author:
- VCU CISTEME .
- Date Added:
- 03/01/2023


Explore the four main phases of the problem-solving process. Analyze a problem and use the steps in the problem-solving process to solve a problem.

Leverage visual-based programming to introduce text-based programming foundation for students.

Basic Programming in Scratch

Students generate and complete presentations demonstrating what they have learned in CS

Students use data to apply statistical concepts and practice fundamental statistical terms.
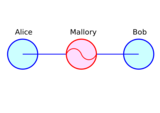
This is an unplugged version of how a man in the middle attack can happen and how data can be altered using rope, binder clips, envelopes and index cards.

This activity will show the sorting process using the Merge Sort Divide and Conquer algorithm that is used by a computer when sorting data without using a computer.

This lesson is used to show how conditionals can help filter a dataset. This lesson uses python and a large csv file of Netflix Content to filter through PG-13 movies and output recommendations based on user genre choce. This lesson can be taught using any python IDE and intended to be a live programming demonstration with students. Students will then extend this concept using a dataset of their own choice or other datasets given to them to explore.
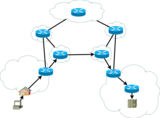
This is an unplugged version of how computer data packets travel through computer networks using rope, binder clips, envelopes and index cards.

Want to introduce some basic coding and real life examples of the Scientific Method? This is the lesson for you. Using either the online program MakeCode, or by purchasing the Handheld Kitronik Arcades, the students will be performing an experiment while coding a maze game. No purchases required if students only use the online platform. A whole lesson ready to engage your students and use Computer Science and the Scientific Method!

Students will learn about abstraction by examining a model computer and then breaking down several medieval romances into their essential components.

Students break down a large task into smaller pieces in this lesson about Wars from 1500.

This is a whole classroom collaborative process with the goal of creating a school-wide lunch waste composting program. The lesson relates the collaborative and iterative processes used in science to computer science.

Students will learn about abstraction by looking at a built model computer and then breaking solving a system of equations down into simple components.

In this lesson, students will have a brief introduction to creating an app in Code.org’s App Lab. They will then create an app that will determine if three given lengths can form a triangle or not.

How are predators in the WILD and ONLINE similar? Check out this lesson that incorporates Cybersecurity and pack animals! You will learn ways on how both the animals and you can be protected from danger!

This lesson incorporates computer science with an interesting enrichment topic for Environmental Science II, Astronomy - Dark Matter. Students will be able to visualize WHY scientists believe that 85% of matter in our universe is not the same as what we are made of. Using simple orbital speed kits, your class can combine their data and analyze it to see what happens to orbital speed with increasing distance from the barycenter of a galaxy. They can add mass to the center to represent dark matter and see how that increases the orbital speed - just like what Vera Rubin discovered in the 1960s.

Students learn about how computers represent data visually and how artists have used self portraits with symbolism to represent themselves. Then students will create their own data selfies including adding their names written in binary code. Written descriptions will be added to display alongside their artworks that will detail their data symbols and what their artwork says about them and how it relates to computer science.

Help students read & comprehend sonnets by examining structural components.

Students will discuss concerns related to the increasing use of technology including AI. Items to be discussed are privacy, ethics, and automated collection of data.